Efficiently Manage Oil and Gas Cybersecurity Risks
Organizations in the energy sector are prime targets for cyberattacks. Critical infrastructure, along with many high-value assets that span multiple facilities and remote sites, creates complexity that hides vulnerabilities and makes meeting compliance nearly impossible with manual tools.
In an industry where minor downtime and compliance violations can lead to significant financial losses and environmental hazards, oil and gas cybersecurity from FireMon empowers these organizations to maintain compliance, mitigate cyber risks and avoid operational disruptions.
Why Choose FireMon?
Proactive Threat Response
FireMon helps you quickly identify and respond to threats, ensuring robust network security.
Efficient Compliance Management
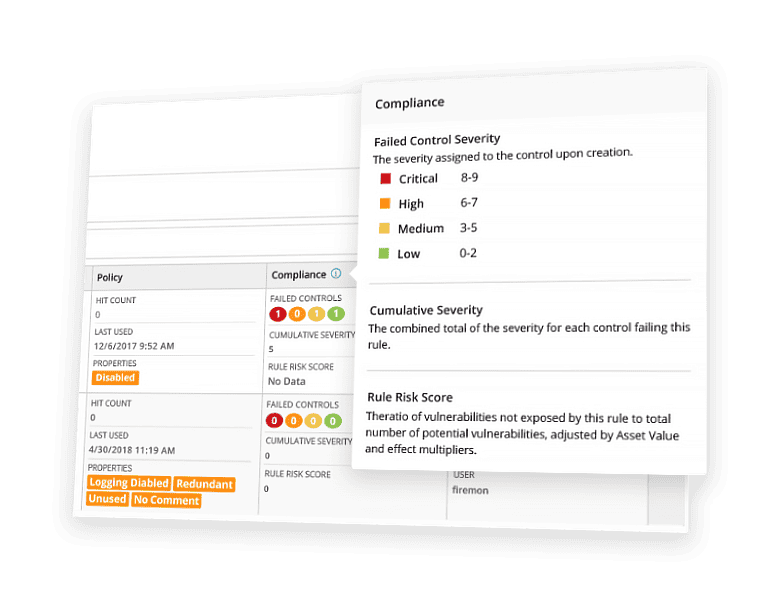
Manage compliance with real-time violation detection and advanced risk modeling.
Scalable Solutions
FireMon’s customizable solutions grow with your organization, protecting your valuable data.
Seamless Compliance with Oil and Gas Cybersecurity Regulations
Stay ahead of ever-changing energy regulations with FireMon’s comprehensive oil and gas cybersecurity compliance solution that simplifies and automates reporting, violation detection, and rule recertification at enterprise scale.
- Oil, Gas, and Energy-Specific Compliance Reporting: FireMon provides built-in assessments, including NIST, ISO 27001 and 27019, SOX, NERC CIP, FERC, and GDPR, while supporting custom assessments using internal business policies, external frameworks, or industry best practices.
- Real-time Violation Detection: Continuous network security monitoring over your entire environment with automated cyber threat alerts that detect violations as they happen helps prevent interruptions that could affect sales and customer confidence.
- Customizable Growth: With performance verified to support 15 thousand devices and 25 million rules coupled with an API-first approach for easy integrations into SIEM, SOAR, vulnerability scanners, and ITSM solutions, FireMon has your current and future security environments covered.
With FireMon’s network security policy management, your energy business stands to benefit from enhanced protection, improved efficiencies, and long-term savings.
Purpose-Built Oil and Gas Cybersecurity Solutions for Complex Environments
FireMon’s solutions prioritize oil and gas cybersecurity by protecting critical infrastructure, industrial networks, and sensitive operational data. With real-time visibility and automated policy management, FireMon helps energy organizations protect against threats, reduce risk across IT and OT environments, and maintain safe, uninterrupted operations.
Our continuous compliance management has been verified to support 15K devices and 25M rules, supporting operational integrity across the energy sector.
Learn More About Network Security andOil and Gas Compliance
Explore the Resource CenterFrequently Asked Questions
What Vulnerabilities are Most Prominent in Cybersecurity for the Oil and Gas Industry?
Oil and gas companies often run on aging technology that wasn’t built with today’s threats in mind. Many facilities still rely on legacy systems and flat networks, which makes it easier for attackers to move through the environment once they gain unauthorized access, disrupting operations.
Add in hard-to-reach sites, limited visibility into connected assets, and spotty patching practices, and you’ve got a landscape where small oil and gas cybersecurity risks can quickly turn into major risks.
What are the Biggest Threats to Cybersecurity in Oil and Gas?
Ransomware attacks are a top threat to oil and gas cybersecurity — and they’re getting smarter. Attackers know how valuable uptime is in the industry, so they go after industrial control systems (ICS) and demand payment fast. Insider threats and nation-state actors also pose serious risks, often looking to steal intellectual property or disrupt supply chains. As IT and OT systems become more connected, the potential fallout from an attack grows, especially in remote or offshore environments where recovery can take time.
What Cybersecurity Solutions for Oil and Gas Should Companies Be Using?
Companies need to start with visibility because you can’t secure what you can’t see. Tools that map out every device, monitor traffic in real time, and enforce access controls are must-haves. Network segmentation helps isolate threats, while automated policy management reduces human error and response times. And because no defense is perfect in the oil and gas sector, having a tested incident response plan and regular audits keeps security efforts sharp and ready.
Why is Cybersecurity in Oil and Gas Industry Practices Important?
Comprehensive cybersecurity isn’t just about protecting data — in oil and gas, it’s about keeping the business running and people safe. A single attack can shut down production, impact energy infrastructure, and even create safety hazards in the field. With so much at stake, strong cyber defenses are crucial to ensuring reliability, adding a layer of risk management, staying compliant, and maintaining trust in one of the world’s most essential industries.
How Does Zero-Trust Cybersecurity for Oil and Gas Improve Security Posture?
Zero Trust enhances cybersecurity in oil and gas environments by assuming no device or user should be trusted by default—whether inside or outside the network perimeter. This approach is especially effective in complex OT and IT ecosystems where outdated systems, remote assets, and third-party vendors introduce risk.
By enforcing strict identity verification, access controls, and continuous monitoring, Zero Trust limits lateral movement and minimizes the blast radius of a breach. For oil and gas organizations, this means stronger segmentation between IT and OT networks, faster threat detection, and greater control over who can access critical infrastructure—improving security posture while reducing operational risk.
What Types of Cybersecurity Vulnerabilities are Present in the Oil and Gas Industry?
Oil and gas companies face a unique blend of cybersecurity vulnerabilities due to aging systems, geographically dispersed assets, and increasing IT/OT convergence. Common vulnerabilities include:
- Legacy Technology: Many industrial systems weren’t designed with security in mind and lack basic protections like encryption or authentication.
- Flat Network Architectures: Without segmentation, attackers can easily move across systems once they gain a foothold.
- Remote Access Risks: Third-party contractors and remote workers often connect to critical systems, increasing exposure to unauthorized access or credential abuse.
- Unpatched Devices: Long patch cycles, especially in offshore or remote locations, create prolonged windows of vulnerability.
- Malware & Ransomware: As highlighted in recent attacks, ransomware is used to shut down ICS environments and demand fast payouts.
- Phishing & Insider Threats: Human error and insider misuse remain persistent challenges in high-stakes industrial settings.
- AI-powered Threats: Adversaries are increasingly leveraging AI to bypass traditional defenses and target supply chain vulnerabilities.
With so many interdependent technologies in play, a vulnerability in one part of the network can cascade into widespread disruption. That’s why comprehensive visibility, policy automation, and continuous risk monitoring are essential to staying secure.